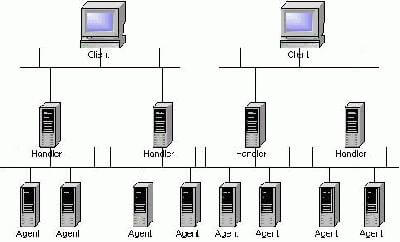
Three-level command structure of computers is characteristic of DDoS attacks
Computer attacks that flood Internet sites with monsoon-intensity deluges of bogus messages made headlines in 2000, when they took down high-profile portals like Yahoo, Amazon and Ebay for several hours — and continue unabated today. Now, a team from ISI is developing a sophisticated, automated process to make defense both more powerful and more automatic.
Their research, called COSSACK (Coordinated Suppression of Simultaneous Attacks), is being funded by a $1.2 million grant from the Defense Advanced Research Projects Agency.”Rather than passively waiting for attacks to occur,” said Christos Papadopoulos, an ISI researcher and an assistant professor in the Engineering School’s department of Computer Science who directs this effort, “COSSACK will put automatic cops, in the form of a network of dedicated security computers, on the job proactively monitoring the Internet for danger signs. These computers will be able both to act themselves, autonomously, when they detect such signs, and also to enlist the aid of their computer colleagues and human personnel.”
Attacks, typically the work of pranksters, often working from outside the United States, may no longer make headlines, but have hardly ceased: A recent study found that more than 4000 such attacks occur every week.
Most attacks today are aimed at small, non-commercial sites, and most succeed, because overworked system operators in most commercial sites don’t have the time or resources to deal with them.
At the larger operations, skilled operators have learned to thwart such attacks, but they still must deal with each attack by hand, in real time, using a complicated set of commands and techniques.
As an indication of how difficult such defense can be, in May of this year, the website for the Computer Emergency Response Team/Coordination Center (CERT) — a federally funded, central computer security resource for the entire information technology community — was intermittently unavailable for days.
And even the limited defensive success so far achieved has become increasingly precarious as attackers learn new tricks. And as society becomes more dependent on web services, such attacks increasingly have the potential to cause serious damage.
This is particularly true if criminals or even terrorists focus not on individual websites but on the routers and name servers that service numerous web sites at once. Now, such targets are seldom hit.
Papadopoulos explained that flooding attacks (technically called “Distributed Denial of Service” attacks) are the result of a two-stage stealth process. In the first stage, he said, the attackers seize control of networked computers using virus-like computer programs or software security holes. Typically, the attackers use their own computer to take over an initial group of machines, called “clients.”
The clients are programmed to automatically repeat the process, taking over another set of sub-clients, or “handlers,” which then, in turn, take over still a third layer of machines, called “agents,” or “zombies.”
The structure resembles a terrorist organization, with leaders exerting control over a small staff of subordinates who in turn control cells with active members. And, like a human terrorist cell, captured computers can be programmed to act as “sleepers,” giving no sign of their mission until they are activated by orders passed down through the chain of command.
In the second stage, which can be months or even years after the virus distribution, the actual attack is launched by a signal from the clients. The zombies — who can number in the hundreds, or even thousands — all simultaneously bulk-send messages to a designated target, such as a web server or a router creating a huge volume of incoming traffic. The actual attackers are shielded from identification by time and the numerous intermediaries used — which are also programmed to cover the attackers tracks by hiding their address and locally erasing incriminating traces.
The attacks, from a numerous and highly distributed set of agents, are serious business. “The cueing signal produces thousands of messages per second flooding the address,” Papadopoulos explained.
Very few sites can handle that much traffic in that short a time period. Users are suddenly locked out as the server collapses under the driving blizzard of repetitive messages.
Counter-measures have slightly improved since the earliest attacks, making it possible to speedily set up filters blocking the most common messages sent repetitively by captive computers.
Nevertheless, Papadopoulos said, “attacks continue. Attackers can patrol the Internet at leisure, then find and take over vulnerable machines, one by one. Then, weeks or months later, these can be used in an attack.” The volume of attacks remains high and increasing, with each week bringing more.
More disturbing, the sophistication is increasing, as attackers learn to alter their disruptive messages to get around filters and find better ways to hide their damaging attack tools.
The scientist said COSSACK hopes to change the balance of power by setting up dedicated computers, which will continuously monitor the Internet looking for the telltale signs of messages carrying the enslaving virus.
When these networked computers sense an attack, or distribution of the slave-making virus programs preparatory to an attack, they can themselves act to quarantine or filter the message, as well as bring the problem to the immediate attention of specialists, who can observe the automated response and augment it if necessary.
“We think this will substantially increase security,” Papadopoulos added. He hopes that COSSACK will be ready to patrol the Internet experimentally before the end of 2003, or sooner. “We have a growing problem,” he says. “We hope to have a better mousetrap before we start encountering smarter mice.”
Ramesh Govindan, an ISI project leader and research assistant professor of computer science, worked with Papadopoulos to create the architecture of COSSACK, and Robert Lindell, another ISI computer scientist, is now helping to develop it, along with ISI programmer John Mehringer, and graduate students Xin Li, Krishna Chintalapudi and Christos Siaterlis.
Published on December 7th, 2001
Last updated on June 11th, 2024