Photo credit: LV4260/Getty Images
DNS server attackers don’t have it easy anymore, thanks to a new technology developed at USC Viterbi’s Information Sciences Institute (ISI).
ASM Rizvi, lead research engineer, Jelena Mirkovic, research team lead, John Heidemann, principal scientist, Wes Hardaker senior computer scientist, and Robert Story, research lead, were awarded the Best Paper Award at the IEEE (1) COMSNETS in January 2023.
The team’s paper, “Defending Root DNS Servers Against DDoS Using Layered Defenses,” describes the system they designed to successfully fight incoming attacks on DNS servers.
“We highlighted several real world attack events that we observed in the DNS root server and we showed that using our system, we could have successfully mitigated them,” Rizvi said.
These layered defenses include filtering for “spoofed” or disguised attacker traffic, identifying known-good traffic to let through, and detecting suddenly aggressive DNS clients.
Their paper was chosen for the award out of 34 papers that were accepted into the conference.
Distributed Denial-of-Service (DDoS) Attacks
The Domain Name System, invented at USC Viterbi ISI by Paul Mockapetris, translates website domain names (such as www.google.com) into numerical values (IP addresses) which are needed to route the user requests to the correct server.
Their job, helping a web browser parse a web page address, is crucial in making sure the right page pops up.
Without DNS servers, finding what we need would be a much more time consuming and difficult task.
Unfortunately, they may suffer from Distributed Denial-of-Service (DDoS) attacks, which overwhelm the targeted server with an influx in traffic to disrupt normal traffic flow–it’s like a deliberate highway traffic jam, preventing you from getting to work on time.
DDoS attacks “keep legitimate clients from gaining access to the server,” Rizvi says, because all of its resources are already allocated to fulfilling the attackers’ requests.
Mirkovic added that these DNS servers are “especially challenging to protect against attacks” because they are public servers that are accessed by a variety of customers with a wide range of behaviors.
“So there are some customers that send very little traffic sporadically, maybe a few queries per day and others that send tens of thousands of queries per second, so it’s a big range to be able to model,” Mirkovic explained.
Operation Defend those Servers!
A special role in the DNS operation is played by DNS root servers, which serve as a focal point for many requests.
These root servers direct DNS clients to more specialized DNS servers, which ultimately fulfill their queries, akin to the 411 service humans to find out contact information of various businesses and people.
USC Viterbi ISI is home to the first root server ever. There are only 13 DNS root servers globally, one of which is B-Root, operated exclusively by USC.
B-Root receives billions of requests each day, so the team was able to use its live traffic and data sets to design and test their defenses as a case study.
“Our system was certainly developed and formed from what we learned from B-Root,” Heidemann said.
Their system, called DDiDD–DDoS Defense In Depth for DNS, “contains a collection of defense modules, and when a DNS server is attacked, the system then picks which module to deploy” Heidemann added. It also “knows how and when to change if the original choice doesn’t work.”
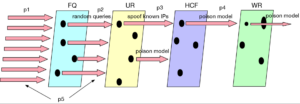
The team’s concept of a layered defense. Heidemann says that “no single one of our different defenses will completely stop an attack, but together they minimize an attack’s effects.”
A successfully developed and proven defense, however, is not the end all be all. Attackers are constantly changing their methods and patterns, which means defenses must adjust accordingly.
“Like most security problems this is an arms race, and if we make it harder, they’ll make it harder still and so on. 5 years from now, what will the modules to defend be? I’m not sure,” Heidemann said.
Bringing Home the Prize
Even with the cyber-attack sphere constantly evolving, the team is proud of their contribution and its utility.
“One of the big goals of the paper was to show that it’s feasible to have an array of defenses and to select which one works best for each attack, and we have shown that it is possible and how to do it,” Heidemann said.
Mirkovic said she was “thrilled” when the paper took home the award.
“We put in a lot of work, and I think it’s an under researched area that doesn’t see a lot of attention, so I think that is part of what made our work stand out,” she added.
Next up is operationalizing the software so that the broader University community can implement it.
We are deploying the system in the real server, and trying to see when new attacks come, whether our system can handle it or not,” Rizvi explained. “Then we can work on enriching the system and making it stronger.”
(1) The IEEE is the largest global professional organization for the advancement of technology. COMSNETS is a conference dedicated to the discussion of innovative technologies in communication and networking systems.
Published on April 18th, 2023
Last updated on May 16th, 2024