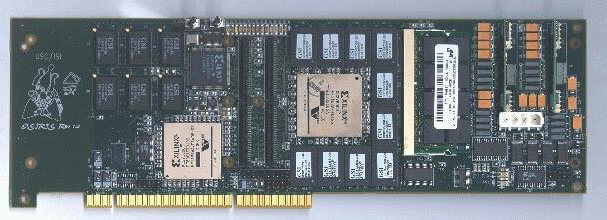
The new SLAAC Osiris FPGA platform is expected to bring GRIP up to full gigabite/sec speed.
A new system developed by ISI East researchers has broken through a critical security bottleneck limiting the usefulness of new, high bandwidth networks.
Tom Lehman, Brian Schott, and Jaroslav Flidr are co-leaders of the ISI team that presented results of recent tests of its GRIP (Gigabit Rate IPsec) high bandwidth security system at the Field-Programmable Custom Computing Machines (FCCM) 2002 conference Tuesday, April 23 in Napa, California. Helping to develop GRIP were researchers at George Mason University.Lehman, a senior programmer at ISI’s campus at Arlington, VA, noted that the speed of networks had outstripped the computing capacity of ordinary desktop computers for many critical tasks.
“Processing unsecured network data in the near gigabit/second range requires nearly 100% of capacity for even high end workstations today,” he explained. “These systems do not have the capacity to handle the additional requirements of secure communications, which include cryptographic and security protocol processing.”
“As a result, users are unable to take advantage of the added bandwidth of gigabit-sec connections when sending secure communications,” Lehman said, going on to note that the advent of newer, 10-gigabit/second networks will further amplify the mismatch between end systems and network capabilities.
The goal of the GRIP project is to offload the processing requirements associated with secure network data communications and free up the resources of the general purpose CPU system for their intended purpose — application processing, he said.
And it does so in a novel fashion. ISI/Arlington computer scientist Jaroslav Flidr explained that the traditional solution to the problem of an overburdened CPU is to add a dedicated accelerator device to handle the special task overflow.
But this solution doesn’t work to serve a gigabit network because the conventional configuration for the added device — on a PCI-based accelerator card — creates a new traffic jam in the computer bus connecting it with the host CPU.
The message for encryption must first be sent from the main CPU to the accelerator, and then from the accelerator back to the main CPU, then from the main CPU to a network interface, he explained. The article presented at the Napa conference notes that “measurements have shown in such a system that the best throughput available with such a system is far below gigabit/sec rates.”
A next generation of more powerful computers with high-speed buses (e.g. Infiniband) will likely eventually solve the problem. But in the meantime, the new GRIP system created by the ISI team uses Field Programmable Gate Arrays (FPGA) — hardware devices which can be reconfigured to optimize processing of different tasks in this case, both the cryptographic transforms and the packet processing.
The key component to GRIP system’s success is the integration of the FPGA-based cryptographic processing with the packet processing and a Gigabit Ethernet network interface, Lehman said. The data goes from the GRIP system to the PC it serves only once either sending or receiving. Tests of the prototype GRIP processor showed that the system was capable of sending fully secured data at 800MB/sec — .8 gigabits per second.
The arrays work within a computing platform that has been developed at ISI/Arlington over the past four years by a project called Systems Level Applications of Adaptive Computing (SLAAC),carried on by a team including Schott and GRIP co-author Peter Bellows.
With improvements now on the drawing board “1 gigabyte per second host-to-host network traffic is expected in the very near future,” according to the presentation. The team based these projections on use of an improved version of the SLAAC-developed platform, called Osiris, which has more logic resources and memory.
GRIP can be configured to use all security protocols currently in wide use, including IPsec’s ESP and AH. The supported cryptographic transforms include 3DES, AES (Rijndael) and SHA-1. Kris Gaj and Pawel Chodowiec from George Mason University developed the cryptographic FPGA cores.
GRIP is the latest successful use of the SLAAC computing platform, according to developer Schott, a project leader at ISI/Arlington. Other applications include a SLAAC-based unit that achieves a 95 percent reduction in size in replacing old circuit boards in the Navy’s Aegis defense system, plus promising initiatives in areas such as sonar, infra-red detection, and high-bandwidth image processing.
In addition to Lehman, Schott, Flidr and Bellows, the GRIP team included Keith D. Underwood,now at Clemson University. The Defense Advance Projects Research Agency (DARPA) Information Technology Office funded the GRIP project as part of its Next Generation Internet Program.
Published on May 4th, 2002
Last updated on August 10th, 2021